Fake site "not t epad-plus-plus.org"
-
Recently registered (December 24, 2020), info redacted from Whois not suprised:
https://who.is/whois/nottepad-plus-plus.org
Resolves to CloudFlare servers:
PS VinsWorldcom ~\source > dig nottepad-plus-plus.org ; <<>> DiG 9.8.1 <<>> nottepad-plus-plus.org ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 18575 ;; flags: qr rd ra; QUERY: 1, ANSWER: 3, AUTHORITY: 0, ADDITIONAL: 0 ;; QUESTION SECTION: ;nottepad-plus-plus.org. IN A ;; ANSWER SECTION: nottepad-plus-plus.org. 300 IN A 104.27.185.137 nottepad-plus-plus.org. 300 IN A 104.27.184.137 nottepad-plus-plus.org. 300 IN A 172.67.147.177 ;; Query time: 121 msec ;; WHEN: Wed Jan 06 11:52:24 2021 ;; MSG SIZE rcvd: 107 PS VinsWorldcom ~\source > dig -x 104.27.185.137 ; <<>> DiG 9.8.1 <<>> -x 104.27.185.137 ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NXDOMAIN, id: 30192 ;; flags: qr rd ra; QUERY: 1, ANSWER: 0, AUTHORITY: 1, ADDITIONAL: 0 ;; QUESTION SECTION: ;137.185.27.104.in-addr.arpa. IN PTR ;; AUTHORITY SECTION: 27.104.in-addr.arpa. 3600 IN SOA cruz.ns.cloudflare.com. dns.cloudflare.com. 2034580120 10000 2400 604800 3600 ;; Query time: 88 msec ;; SERVER: 10.20.200.53#53(10.20.200.53) ;; WHEN: Wed Jan 06 11:52:36 2021 ;; MSG SIZE rcvd: 126 PS VinsWorldcom ~\source > dig -x 172.67.147.177 ; <<>> DiG 9.8.1 <<>> -x 172.67.147.177 ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NXDOMAIN, id: 60765 ;; flags: qr rd ra; QUERY: 1, ANSWER: 0, AUTHORITY: 1, ADDITIONAL: 0 ;; QUESTION SECTION: ;177.147.67.172.in-addr.arpa. IN PTR ;; AUTHORITY SECTION: 67.172.in-addr.arpa. 3398 IN SOA cruz.ns.cloudflare.com. dns.cloudflare.com. 2034580120 10000 2400 604800 3600 ;; Query time: 58 msec ;; SERVER: 10.20.200.53#53(10.20.200.53) ;; WHEN: Wed Jan 06 11:52:46 2021 ;; MSG SIZE rcvd: 126Cheers.
-
A user on reddit saw this too https://www.reddit.com/r/helpme/comments/krezur/notepad/
Here’s what i said on reddit :
///
Whois show that the fake website is russian and was regesitered less than a month ago :- fake https://www.whois.com/whois/nottepad-plus-plus.org
- real https://www.whois.com/whois/notepad-plus-plus.org
The only thing the fake website seems to hide is the trojan in the installers, the donation page seems unchanged
I tested two installer for v 7.9.2 with virustotal :
- fake https://www.virustotal.com/gui/file/3e21c0ebf0b0545b8a39f1c930c438f456002ec552a87b2be0658e858afd78d4/detection
- real https://www.virustotal.com/gui/file/a797da6e8cebe364becc30d3d5d540897166e7674a0fc8e386fd9593d0838f43/detection
U can see the first one seems to hide a trojan, I tested the file with windows defender and it detected nothing, same with Spybot.
I dunno what we can do, maybe send an email to the real owner…
Update : I repported the website to Firefox, Google and Microsoft
///
So if it was not already done I repported it … -
Chrome tried to protect me from going there:
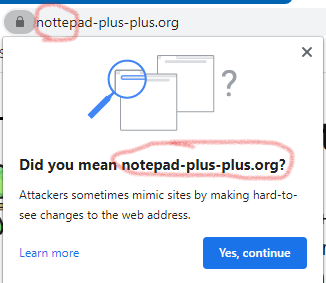
Thanks Chrome! :-)
-
@Michael-Vincent said in Fake site "not t epad-plus-plus.org":
Resolves to CloudFlare servers:
Thank you for your investigation. However, without being a network expert, I’m not sure about the result:
SERVER: 10.20.200.53#53(10.20.200.53)Is the IP of server in which this fake site is hosted
10.20.200.53? What can I do with such info? -
@J-De-Castro said in Fake site "not t epad-plus-plus.org":
Update : I repported the website to Firefox, Google and Microsoft
Thank you for reporting this problem!
Could you share the links where you have reported so I can report to them as well? -
@donho said in Fake site "not t epad-plus-plus.org":
Is the IP of server in which this fake site is hosted 10.20.200.53 ? What can I do with such info?
No, that’s just my internal DNS server that is supplying the result from the recursive lookup.
-
@donho ,
Based on the link @Michael-Vincent sent, the fake domain is using netim as their registrar, and CloudFlare as their DNS server:
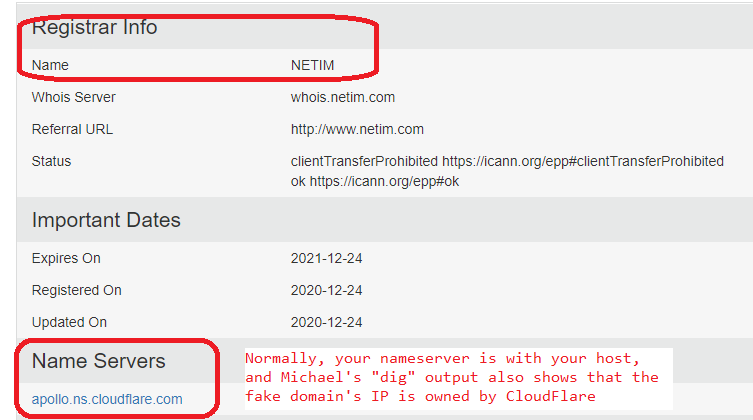
Often, your DNS server is also run by your web host, so I’d say that CloudFlare is the host that owns the machine for the fake domain.
Michael’s
digon the IP confirms that CloudFlare owns the IP address used by the fake domain. That strengthens the conclusion that CloudFlare really is the host.Thus, I believe that contacting CloudFlare, and asking them to take down the spoof site is the right next step
-
@donho
Yep here the adresses I used to repport the website :
https://safebrowsing.google.com/safebrowsing/report_badware/?hl=en
https://www.microsoft.com/en-us/wdsi/support/report-unsafe-site-guestas said by @PeterJones I think the next step is contacting cloudflare to repport the abuse
this can help https://www.namecheap.com/blog/how-to-report-a-fraudulent-website-to-a-registrar/
for repporting to cloudflare :
https://support.cloudflare.com/hc/en-us/articles/360028158352-Reporting-abuse-to-Cloudflare#h_eb67da7f-6013-45a5-a9c8-6b71327190a1
https://www.cloudflare.com/abuse/formHope this can be resolved fast
-
Thank you @Michael-Vincent @PeterJones & @J-De-Castro for your help.
Just tweeted it:
https://twitter.com/Notepad_plus/status/1347757857056423936And also create a ticket in CloudFare with the following content - I have a CloudFare account, since
notepad-plus-plus.orguses some service of CloudFare:A fake site of Notepad++ under the domain "nottepad-plus-plus.org" has the same look and content as the real one, except the distributed binaries (Notepad++ packages & installers). In this site the malware is distributed. After some digging, the fake domain is using netim as their registrar, and CloudFlare as their DNS server. it could be that CloudFlare is the host that owns the machine for the fake domain. Could you check from your site if you host this fake website (and of course take it down if it's the case) please? Thank you in advanceLet’s wait & see.
-
@donho said in Fake site "not t epad-plus-plus.org":
At that twitter link @donho has 2 links where we can go to report the bad nottepad site. If a lot of people follow the links and do it, I’d think it would help.